Edward Snowden 10 Trues
| Edward Snowden | |
|---|---|
 |
|
| Born | Edward Joseph Snowden June 21, 1983 Elizabeth City, North Carolina, U.S. |
| Residence | Russia (temporary asylum) |
| Nationality | American |
| Occupation | System administrator |
| Employer | Booz Allen Hamilton Kunia Camp, Hawaii, U.S. (until June 10, 2013) |
| Known for | Revealing details of classified United States government surveillance programs |
| Website | www |
| Signature | |
Edward Joseph Snowden (born June 21, 1983) is an American computer professional, former Central Intelligence Agency (CIA) employee, and former contractor for the United States government who copied and leaked classified information from the National Security Agency (NSA) in 2013 without authorization. His disclosures revealed numerous global surveillance programs, many run by the NSA and the Five Eyes Intelligence Alliance with the cooperation of telecommunication companies and European governments.
In 2013, Snowden was hired by an NSA contractor, Booz Allen Hamilton, after previous employment with Dell and the CIA. On May 20, 2013, Snowden flew to Hong Kong after leaving his job at an NSA facility in Hawaii, and in early June he revealed thousands of classified NSA documents to journalists Glenn Greenwald, Laura Poitras, and Ewen MacAskill. Snowden came to international attention after stories based on the material appeared in The Guardian and The Washington Post. Further disclosures were made by other publications including Der Spiegel and The New York Times.
On June 21, 2013, the U.S. Department of Justice unsealed charges against Snowden of two counts of violating the Espionage Act of 1917 and theft of government property.Two days later, he flew into Moscow's Sheremetyevo Airport, but Russian authorities noted that his U.S. passport had been cancelled and he was restricted to the airport terminal for over one month. Russia ultimately granted him right of asylum for one year, and repeated extensions have permitted him to stay at least until 2020. He reportedly lives in an undisclosed location in Moscow, and continues to seek asylum elsewhere in the world.
One year ago, the Guardian published its first bombshell story based on leaked top-secret documents showing that the National Security Agency was spying on American citizens.
At the time, journalist Glenn Greenwald and the Guardian never mentioned that they had a treasure trove of other NSA documents, nor that they came from one person. Then three days later, the source surprisingly unmasked himself: His name was Edward Snowden.
IMAGE: JOHN MINCHILLO/ASSOCIATED PRESS
When asked if more revelations were in the pipeline, Greenwald always used to respond that yes, many more were coming — and he wasn't kidding. Over the next year, explosive stories began to trickle out of those documents. Here are the top 10 revelations of the year.
1. Secret court orders allow NSA to sweep up Americans' phone records
The very first story revealed that Verizon had been providing the NSA with virtually all of its customers' phone records. It soon was revealed that it wasn't just Verizon, but virtually every other telephone company in America.
This revelation is still one of the most controversial ones. Privacy advocates have challenged the legality of the program in court, and one Judge deemed the program unconstitutional and "almost Orwellian," while another one ruled it legal.
The uproar caused by this first story has led President Barack Obama to endorse a reform to the program, and the House of Representatives to pass the first law that tries to change it.
2. PRISM
The existence of PRISM was the second NSA bombshell, coming less than 24 hours after the first one. Initially, reports described PRISM as the NSA's program to directly access the servers of U.S tech giants like Google, Facebook, Microsoft and Apple, among others.
Its reality was slightly different.
PRISM, we soon learned, was less less evil than first thought. In reality, the NSA doesn't have direct access to the servers, but can request user data from the companies, which are compelled by law to comply.
PRISM was perhaps as controversial as the first NSA scoop, prompting technology companies to first deny any knowledge of it, then later fight for the right to be more transparent about government data requests. The companies ended up partially winning that fight, getting the government to ease some restrictions and allow for more transparency.
3. Britain's version of the NSA taps fiber optic cables around the world
The British spy agency, the Government Communications Headquarters (GCHQ), taps fiber optic cables all over the world to intercept data flowing through the global Internet, we learned. The GCHQ works closely with the NSA, sharing data and intelligence in a program that's codenamed Tempora.
Tempora is one of the key NSA/GCHQ programs, allowing the spy agencies to collect vasts troves of data, but for some reason, it has sometimes been overlooked. After a couple of months from the Tempora revelation, a German newspaper revealed the names of the companies that collaborate with the GCHQ in the Tempora program: Verizon Business, British Telecommunications, Vodafone Cable, Global Crossing, Level 3, Viatel and Interoute.
4. NSA spies on foreign countries and world leaders
IMAGE: CHARLES DHARAPAK/ASSOCIATED PRESS
Over the months, countless stories based on Snowden documents have revealed that the NSA has spied on numerous world leaders and foreign governments.
The German newsweekly Der Spiegel revealed that the NSA targets at least 122 world leaders.
Other stories over the past years have named specific targets like German Chancellor Angela Merkel, Brazil's President Dilma Roussef, and Mexico's former President Felipe Calderon, the French Foreign Ministry, as well as leaders at the 2010 G8 and G20 summits in Toronto.
5. XKeyscore, the program that sees everything
XKeyscore is a tool the NSA uses to search "nearly everything a user does on the Internet" through data it intercepts across the world. In leaked documents, the NSA describes it as the "widest-reaching" system to search through Internet data.
6. NSA efforts to crack encryption and undermine Internet security
Encryption makes data flowing through the Internet unreadable to hackers and spies, making the NSA's surveillance programs less useful. What's the point of tapping fiber optic cables if the data flowing through them is unreadable? That's why the NSA has a developed a series of techniques and tricks to circumvent widely used web encryption technologies.
The NSA, however, isn't able to compromise the encryption algorithms underlying these technologies. Instead, it circumvents or undermines them, forcing companies to install backdoors, hacking into servers and computers, or promoting the use weaker algorithms.
In any case, technologists were alarmed.
"Even as the NSA demands more powers to invade our privacy in the name of cybersecurity, it is making the Internet less secure and exposing us to criminal hacking, foreign espionage, and unlawful surveillance. The NSA's efforts to secretly defeat encryption are recklessly shortsighted and will further erode not only the United States' reputation as a global champion of civil liberties and privacy but the economic competitiveness of its largest companies," Christopher Soghoian, principal technologist at the American Civil Liberties Union (ACLU) said at the time.
7. NSA elite hacking team techniques revealed
The NSA has at its disposal an elite hacker team codenamed "Tailored Access Operations" (TAO) that hacks into computers worldwide, infects them with malware and does the dirty job when other surveillance tactics fail.
Der Spiegel, which detailed TAO's secrets, labelled it as "a squad of plumbers that can be called in when normal access to a target is blocked." But they can probably be best described as the NSA's black bag operations team.
TAO comes in for specific, targeted operations when the NSA can't find intelligence or needs more detailed information on a target through its bulk surveillance programs. Before Snowden, most of their operations and techniques were shrouded in secrecy, and their secrets make for one of the most fascinating revelations.
8. NSA cracks Google and Yahoo data center links
When bulk collection or PRISM fails, the NSA had other tricks up its sleeve: It could infiltrate links connecting Yahoo and Google data centers, behind the companies' backs.
This revelation was made famous mostly by a Power Point slide that included a celebratory smiley face.
This story truly enraged the tech companies, which reacted with much more fury than before. Google and Yahoo announced plans to strengthen and encrypt those links to avoid this kind of surveillance, and a Google security employee even said on his Google+ account what many others must have thought privately: "Fuck these guys."
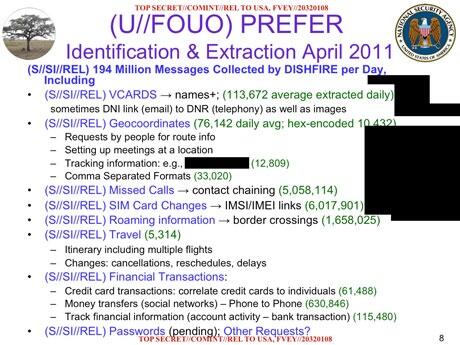
9. NSA collects text messages
It's not just about Internet data though. The NSA, following its unofficial motto of "collecting it all," intercepts 200 million text messages every day worldwide through a program called Dishfire.
In leaked documents, the agency described the collected messages as a "goldmine to exploit" for all kinds of personal data.
Other documents also revealed that the NSA can "easily" crack cellphone encryption, allowing the agency to more easily decode and access the content of intercepted calls and text messages.
10. NSA intercepts all phone calls in two countries
The NSA intercepts and stores all phone calls made in the Bahamas and Afghanistan through a program called MYSTIC, which has its own snazzy logo.
The Bahamas was revealed by The Intercept, Greenwald's new website, while the second was revealed by WikiLeaks, which protested The Intercept's decision to withhold the second country's name.
The NSA also collects all phone calls' metadata in Mexico, Kenya and the Philippines.
SOURCE: mashable







No comments